Hi Anca, it is just as puzzling to me, actually.
Only thing I know that could have caused this was to add these two lines to the compose file:
- SNAPSHOT_SAVE_STRATEGY=SCHEDULED
- SNAPSHOT_LOAD_STRATEGY=ON_STARTUP
I shut down the container, added the flags and booted it back up - instantly, my S3 requests were failing. I added them cause I saw the following info in the log files:
2024-03-08T14:00:04.895 WARN --- [ MainThread] l.p.snapshot.plugins : registering ON_REQUEST load strategy: this strategy has known limitations to not restore state correctly for certain services
2024-03-08T14:00:05.348 INFO --- [ MainThread] l.p.snapshot.plugins : registering SCHEDULED save strategy
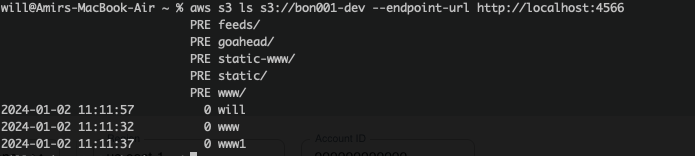
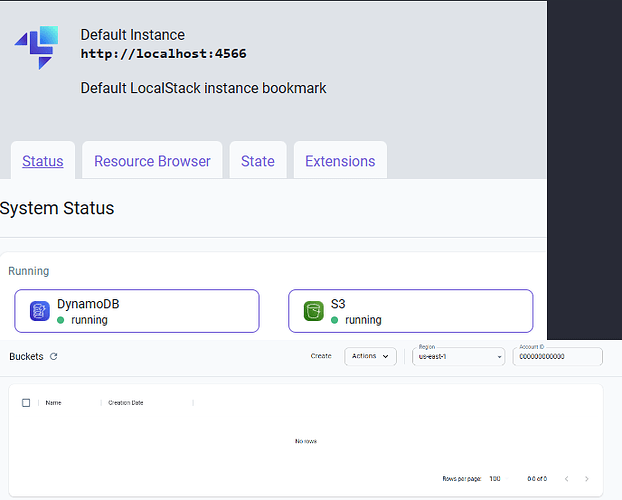
here are some shots of the bucket and the web ui:
# ls -al
total 24
drwxr-xr-x 5 root root 4096 Nov 23 22:49 .
drwxr-xr-x 7 root root 4096 Mar 4 18:55 ..
-rw-rw-r-- 1 root root 58 Mar 8 15:34 api_states.json
drwxr-xr-x 2 root root 4096 Mar 8 14:36 dynamodb
drwxr-xr-x 2 root root 4096 Nov 23 22:48 dynamodbstreams
drwxr-xr-x 3 root root 4096 Nov 23 22:49 s3
# cd s3
# ls -al
total 16
drwxr-xr-x 3 root root 4096 Nov 23 22:49 .
drwxr-xr-x 5 root root 4096 Nov 23 22:49 ..
drwxr-xr-x 2 root root 4096 Feb 3 21:41 novelcrafter-novel-storage
-rw-r--r-- 1 root root 259 Mar 7 19:48 store.state
# cd novelcrafter-novel-storage
# ls -al
total 1852
drwxr-xr-x 2 root root 4096 Feb 3 21:41 .
drwxr-xr-x 3 root root 4096 Nov 23 22:49 ..
-rw-r--r-- 1 root root 11209 Mar 7 19:48 codex_2V7wslgVGwSxGwZz3qijvdSFmL8_thumbnails_2Yb2j3g3lp6jHURrhaMOtfqvdYj.jpg_8328f105_null
-rw-r--r-- 1 root root 15489 Mar 7 19:48 codex_2V7wsn9u1ANUmsykasPnmOM8Cja_thumbnails_2Yb2XdAOovH5zKDeKhMa91qQufP.jpg_a87cbdb6_null
-rw-r--r-- 1 root root 9536 Mar 7 19:48 codex_2V7wsocWYLZRElMPmsGZ43S7FRi_thumbnails_2Yb2eVLfruvBjc7Dce00KGvO0P4.jpg_72cfa595_null
-rw-r--r-- 1 root root 14356 Mar 7 19:48 codex_2V7wsq8cdPNpsGLLvy2gbyOySIJ_thumbnails_2Yb2wyZhufLRvqRMgUb0meNHmGm.jpg_da6407d0_null
-rw-r--r-- 1 root root 15448 Mar 7 19:48 codex_2V7wssUIDWU91sbReBJTv9My21h_thumbnails_2Yb2mOnp1g5BhtXCzlE2KZhrQVG.jpg_94dfd15f_null
-rw-r--r-- 1 root root 10812 Mar 7 19:48 codex_2V7xcSGuY8HUUderVU4g5XzsJV8_thumbnails_2Yb2klzO5QaVYOKo7SXODyn09Ir.jpg_41de3eee_null
-rw-r--r-- 1 root root 13350 Mar 7 19:48 codex_2V7yOVf70ixxFUmhgvpX7iB1Ura_thumbnails_2Yb30GBI0yVmkmxVa4nYTm7GEox.jpg_3845d55c_null
-rw-r--r-- 1 root root 15745 Mar 7 19:48 codex_2V7yOX8fjgO8XWN9p9RA1lx0RgO_thumbnails_2Yb33v50nfVP4LCGNTzlw5Gz9gf.jpg_8f671f95_null
-rw-r--r-- 1 root root 15081 Mar 7 19:48 codex_2V7yOZ1Gau4bymogK6uX0suDpbA_thumbnails_2Yb2pZK6BpiaY3y9BtBiK5906T5.jpg_f26b1a49_null
-rw-r--r-- 1 root root 13974 Mar 7 19:48 codex_2V7yObioW6HKOSXHK53cr1uzCrZ_thumbnails_2Yb2cVbVqp7Yi2FrvkGS8cWmVuV.jpg_28a90ce1_null
-rw-r--r-- 1 root root 14560 Mar 7 19:48 codex_2V7zL2zJnnx0wrgNmxi7I4SGX1X_thumbnails_2Yb31sadlQFD0rG9SvOu6rMYFUr.jpg_67556551_null
-rw-r--r-- 1 root root 9962 Mar 7 19:48 codex_2VMB2UfExByp8uB60qNStKtecvH_thumbnails_2Yb3638WOrOukTAVIRRczoJAREP.jpg_0665ea2b_null
-rw-r--r-- 1 root root 14581 Mar 7 19:48 codex_2VMB3O3NmrQ8a2V8h7MBSb3pAdT_thumbnails_2Yb37AYwMtvPxjdtjnQdurlhwnt.jpg_5eab340f_null
-rw-r--r-- 1 root root 21340 Mar 7 19:48 codex_2VMYSRlOCWF2HSjr1jF6zVwB83I_thumbnails_2Yb339hdo04268PbY0RVFjw1Byk.jpg_eef497e7_null
-rw-r--r-- 1 root root 12839 Mar 7 19:48 codex_2VqSZRkY5nBsZZwz2B2x8nBE267_thumbnails_2Yb2Z84oSIsRF7oAUn5JXgaCzcb.jpg_0f88a69f_null
-rw-r--r-- 1 root root 15561 Mar 7 19:48 codex_2VqSbDh6whLGxJGkrhLBE2gLvhQ_thumbnails_2Yb2b52iUfjg6IrQQyBqN6Um5uZ.jpg_e258bb71_null
-rw-r--r-- 1 root root 16649 Mar 7 19:48 codex_2YijqWSv8bH0iwTH4oVCA98JDPz_thumbnails_2Yijrt1BjSsX8XvLo8emLDlWLgi.jpg_536449f6_null
-rw-r--r-- 1 root root 22054 Mar 7 19:48 codex_2YjBpTWxXhfUoK7q4aNY5zt3CsA_thumbnails_2YjBr9MUSpsWfo1IQZx3iYpX3il.jpg_5962c92e_null
-rw-r--r-- 1 root root 10861 Mar 7 19:48 codex_2ZdM1Sr1Nqng6qw8hfxaKkZm97I_thumbnails_2ZdM7yEcKhSjqkq6HcWOCbbJ9fE.jpg_3b3d42b4_null
-rw-r--r-- 1 root root 13331 Mar 7 19:48 codex_2bsGaaqP7UwY8JXAXLtnspwj0Ck_thumbnails_2bsGiEBsNVyMRDox6FeVjRnQEoB.jpg_0f96c703_null
-rw-r--r-- 1 root root 18150 Mar 7 19:48 codex_2bsGaaqP7UwY8JXAXLtnspwj0Ck_thumbnails_2bsGjmOpZ34RiHzjKmA2ARSLdiu.jpg_0b9ba437_null
-rw-r--r-- 1 root root 16799 Mar 7 19:48 codex_2bsGaaqP7UwY8JXAXLtnspwj0Ck_thumbnails_2bsGkh1oPnuZeqcBkSecpG0eT4f.jpg_5f195dba_null
-rw-r--r-- 1 root root 174588 Mar 7 19:48 novels_2V5BBk8BriKklAiZw5eZiEAzNnf_covers_2Yb2APTm4dMyAlYQqBCEJguJo6h.jpg_7bceebf6_null
-rw-r--r-- 1 root root 116301 Mar 7 19:48 novels_2VDkc4NlRNGp8cG56bQbC5cJaCL_covers_2Yb2BLKzsuVaK0g74lEcg2aGfNg.jpg_7a5980da_null
-rw-r--r-- 1 root root 130966 Mar 7 19:48 novels_2VDkyfqmTLwx51NlYw97LUEzxqz_covers_2Yb2CE8cVtoq6TznpsV48QV7RN2.jpg_3e74ef17_null
-rw-r--r-- 1 root root 140761 Mar 7 19:48 novels_2VDl1Kuuj0tgTYcDkIsF6pzrbCq_covers_2Yb2DNRGQdjZYwZRzFdU6x14eQk.jpg_93c24d66_null
-rw-r--r-- 1 root root 136190 Mar 7 19:48 novels_2VDl3hu1Mdh8AIyFzAvEr0CQuIq_covers_2Yb2ELzPkCY5rbyJORNCaxueSwt.jpg_cd87f6b7_null
-rw-r--r-- 1 root root 152069 Mar 7 19:48 novels_2VDlhZPvXHavzrBdSvDYBXoaRMl_covers_2Yb28vPDKzC3G6gAwMeboEdJ1mc.jpg_a9e78fe9_null
-rw-r--r-- 1 root root 115600 Mar 7 19:48 novels_2X5kTy7v9ByJ4iaMxGRvtgmnSfs_covers_2Yb25OGrTfPktInrlm0TL39pHCu.jpg_bac6142a_null
-rw-r--r-- 1 root root 161928 Mar 7 19:48 novels_2X5qAavqgwVXw82dQdYNcwBg7Ma_covers_2Yb27y5k0obpmiZdseUNr7qddMm.jpg_f3c2231e_null
-rw-r--r-- 1 root root 123495 Mar 7 19:48 novels_2XJcHNvpQnfM8etREropV8g0dgB_covers_2ZdMJml6rChioW7jpGm8xlFtuCf.jpg_4e11b6e6_null
-rw-r--r-- 1 root root 129574 Mar 7 19:48 novels_2XM1D4epo6bz1AmiZHrmd32ePm8_covers_2Yb26twevHwa6Ixt1LfJsVmewTx.jpg_cf958469_null
-rw-r--r-- 1 root root 112107 Mar 7 19:48 novels_2Ygos0iwAYsalTz0eJX864IvW7E_covers_2YiTlZDcReQfI9XVD26yfwSOBqx.jpg_a8afa833_null
and my log output:
novelcrafter_localstack_main | 2024-03-08T15:08:37.472 WARN --- [ asgi_gw_3] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.473 INFO --- [ asgi_gw_3] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.473 WARN --- [ asgi_gw_1] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.473 WARN --- [ asgi_gw_4] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.474 WARN --- [ asgi_gw_5] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.474 WARN --- [ asgi_gw_2] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.474 WARN --- [ asgi_gw_0] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.475 INFO --- [ asgi_gw_1] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.475 INFO --- [ asgi_gw_4] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.476 INFO --- [ asgi_gw_5] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.477 INFO --- [ asgi_gw_2] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.477 INFO --- [ asgi_gw_0] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.797 WARN --- [ asgi_gw_3] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.798 WARN --- [ asgi_gw_4] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.798 WARN --- [ asgi_gw_2] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.798 WARN --- [ asgi_gw_1] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.799 WARN --- [ asgi_gw_5] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.799 INFO --- [ asgi_gw_3] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.799 WARN --- [ asgi_gw_0] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:37.800 INFO --- [ asgi_gw_4] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.800 INFO --- [ asgi_gw_2] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.800 INFO --- [ asgi_gw_1] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.801 INFO --- [ asgi_gw_5] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:37.801 INFO --- [ asgi_gw_0] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:38.122 WARN --- [ asgi_gw_3] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:38.123 WARN --- [ asgi_gw_2] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:38.123 WARN --- [ asgi_gw_1] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:38.123 INFO --- [ asgi_gw_3] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:38.124 WARN --- [ asgi_gw_5] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:38.124 WARN --- [ asgi_gw_4] l.s.s3.presigned_url : Signatures do not match, but not raising an error, as S3_SKIP_SIGNATURE_VALIDATION=1
novelcrafter_localstack_main | 2024-03-08T15:08:38.124 INFO --- [ asgi_gw_2] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:38.125 INFO --- [ asgi_gw_1] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:38.125 INFO --- [ asgi_gw_5] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:38.126 INFO --- [ asgi_gw_4] localstack.request.aws : AWS s3.GetObject => 404 (NoSuchBucket)
novelcrafter_localstack_main | 2024-03-08T15:08:50.349 INFO --- [read-4 (run)] l.persistence.manager : Saving state for dynamodb took 1 ms
novelcrafter_localstack_main | 2024-03-08T15:08:50.349 INFO --- [read-4 (run)] l.p.snapshot.manager : Saving snapshot to disk took 0.00 seconds
novelcrafter_localstack_main | 2024-03-08T15:11:37.960 INFO --- [ asgi_gw_4] localstack.request.aws : AWS dynamodb.Query => 200
novelcrafter_localstack_main | 2024-03-08T15:11:37.975 INFO --- [ asgi_gw_0] localstack.request.aws : AWS dynamodb.Query => 200